The U.S. National Security Agency (NSA), in the role of protector of U.S. citizens, wants to watch over the Internet and its users through backdoor mechanisms and/or code breaking. This “weak encryption” policy has its “strong encryption” opponents who argue government surveillance of Internet companies, users, and foreign governments violates the fundamental constitutional rights of privacy and liberty. According to the Electronic Freedom Foundation, 150 organizations support this open letter to the President of the United States:
“…reject any proposal that U.S. companies deliberately weaken the security of their products. We request that the White House instead focus on developing policies that will promote rather than undermine the wide adoption of strong encryption technology. Such policies will in turn help to promote and protect cybersecurity, economic growth, and human rights, both here and abroad [1].”
Who is right, and who is wrong? How might an objective policy analysis be performed?
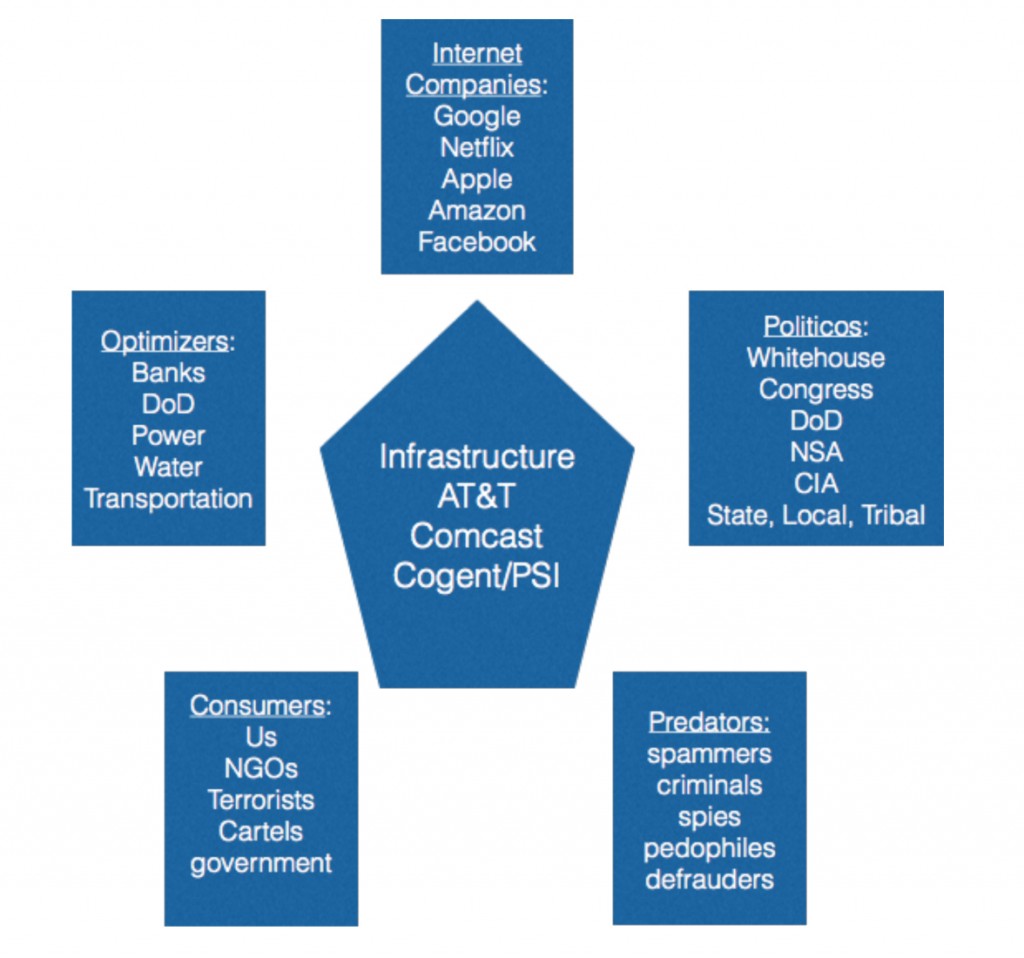
The figure below approximates the system of systems we call the “Internet.” Its components are:
- The Infrastructure. Cables, servers, and software that make up the Internet.
- Internet companies: The providers or services and applications running on the Internet,
- Optimizers: Companies that use the Internet, but do little to develop or control it.
- Consumers: Users, non-governmental organizations, terrorists, cartels, and governmental organizations that use the applications and services provided by the Internet.
- Predators: Spammers, criminals, spies, pedophiles, and defrauders who prey on Internet users.
- Politicos: Various governmental agencies that pass laws, implement regulations, and watch over the Internet.
This simplification is sufficient to perform a policy analysis that looks at the benefits and drawbacks of policy decisions. More importantly, analysis of this system of systems leads to an exploration of potential unintended consequences of a policy. These unintended consequences may be worse than the policy, itself.
Strong Encryption
A policy of strong encryption means the government—or anyone else—cannot break the encryption standard. It guarantees authentication, confidentiality, integrity, and non‐repudiation as defined by the IEEE 509 PKI standard. This has implications for each of the parties shown in the figure above and listed here.
- The Infrastructure: secure transactions, greater resilience
- Internet companies: consumer trust, global markets, trade secrets, less regulation
- Optimizers: security, resilience
- Consumers: more trust, less convenience, protect predators
- Predators: clandestine actions, protect predators, less anonymous
- Politicos: protect constitutional rights, make voters happy, government is less transparent.
Weak Encryption
As you can see, there are both positive and negative aspects of strong encryption. Similarly, there are positive and negative aspects of weak encryption:
- The Infrastructure: promotes surveillance.
- Internet companies: good for business, bad for protecting trade secrets, more regulation.
- Optimizers: promote surveillance.
- Consumers: promote surveillance.
- Predators: expose bad guys, less anonymity, easier for law enforcement.
- Politicos: authorize surveillance, make companies unhappy, and raise constitutional issues.
By default, we already have weak encryption without a clear‐cut policy from the government on surveillance. In a sense, we have the worst of both worlds—no guarantees of security or freedom from surveillance.
Unintended Consequences
On the other hand, an encryption policy that allows for governmental surveillance may stimulate unintended consequences. I list only a handful of the most obvious potential consequences of weak encryption, here:
- The Infrastructure: regionalization and a forked Internet, censorship
- Internet companies: go offshore, reduced revenue
- Optimizers: rise of proprietary networks, loss of interoperability
- Consumers: reduced consumerism, fragmented markets
- Predators: development of proprietary encryption, invention of workarounds
- Politicos: legal challenges, over-regulation, abuse of power.
For example, the vast global infrastructure we call the Internet is actually a collection of regionalized networks all operating on TCP/IP and open-source software. If the U.S. adopts a weak encryption policy, might this force other countries to withdraw from the United Nations of Internet? Regionalization may lead to a fork in the code base of the open source Internet, with corresponding censorship and loss of interoperability. The Internet would become horribly fragmented, which threatens it very existence.
Internet companies may go offshore to avoid legislation. This is already beginning to happen with drone technology as the U.S. FAA policy on drones reduces innovation and drives innovative companies, like Amazon, to move their drone experiments outside of the U.S. The consequences are obvious—less revenue for U.S. Internet companies.
Similarly, the optimizing companies like banks, electric power utilities, and transportation companies may be motivated to develop their own proprietary networks away from prying government eyes. The corresponding loss of interoperability would condemn these fundamental enterprises to decades of inefficiency and unnecessary expense.
Take away the ease of use of the Internet and add vulnerability to intervention by law enforcement, and the predators may be forced to develop their own proprietary encryption that cannot be cracked by the NSA. It is not difficult to create codes with longer keys, more complex hashing algorithms, and undecipherable keys. At the least, surveillance of weak encryption promotes workarounds by the bad guys.
Finally, the politicos may incur endless legal battles over constitutional issues if the NSA or any other official government agency attempts surveillance of emails, online browsing, GPS traces, etc. Weak encryption raises issues of freedom of speech and expression versus stalking, terrorist recruiting, and pedophilia; privacy rights versus public safety; hactivism versus right of assembly; and censorship versus posting of exploit software, criminal recruitment, and online bullying.
References
[1] Kayyali, N. EFF Joins Nearly 150 Organizations, Security Experts, and Companies to Urge President Obama to Support Strong Encryption. Electronic Freedom Foundation. May 19, 2015.

